Reliable SoC Design and Implementation of SHA-3-HMAC Algorithm with Attack Protection | Semantic Scholar

What is the need of xor-ing the key with an outer and inner pad in HMAC? - Cryptography Stack Exchange

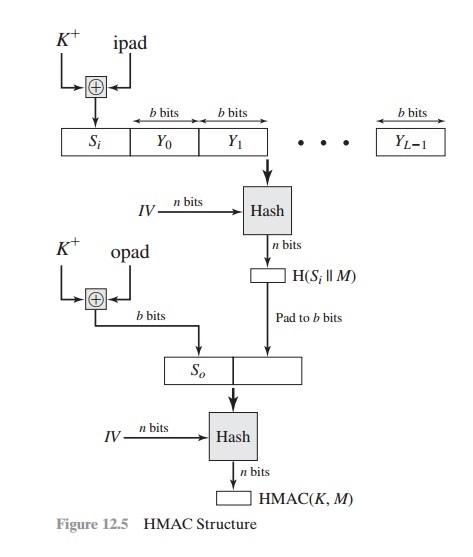
Basic HMAC generation For a recap, in Fig. 1, HASH stands for the hash... | Download Scientific Diagram
![PDF] Deploying Modified Hash Based Message Authentication Code HMAC in MATLAB Using GUI Controls | Semantic Scholar PDF] Deploying Modified Hash Based Message Authentication Code HMAC in MATLAB Using GUI Controls | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b88827b6141fc00aa8980c66d7e37184b0160ed9/4-Figure9-1.png)

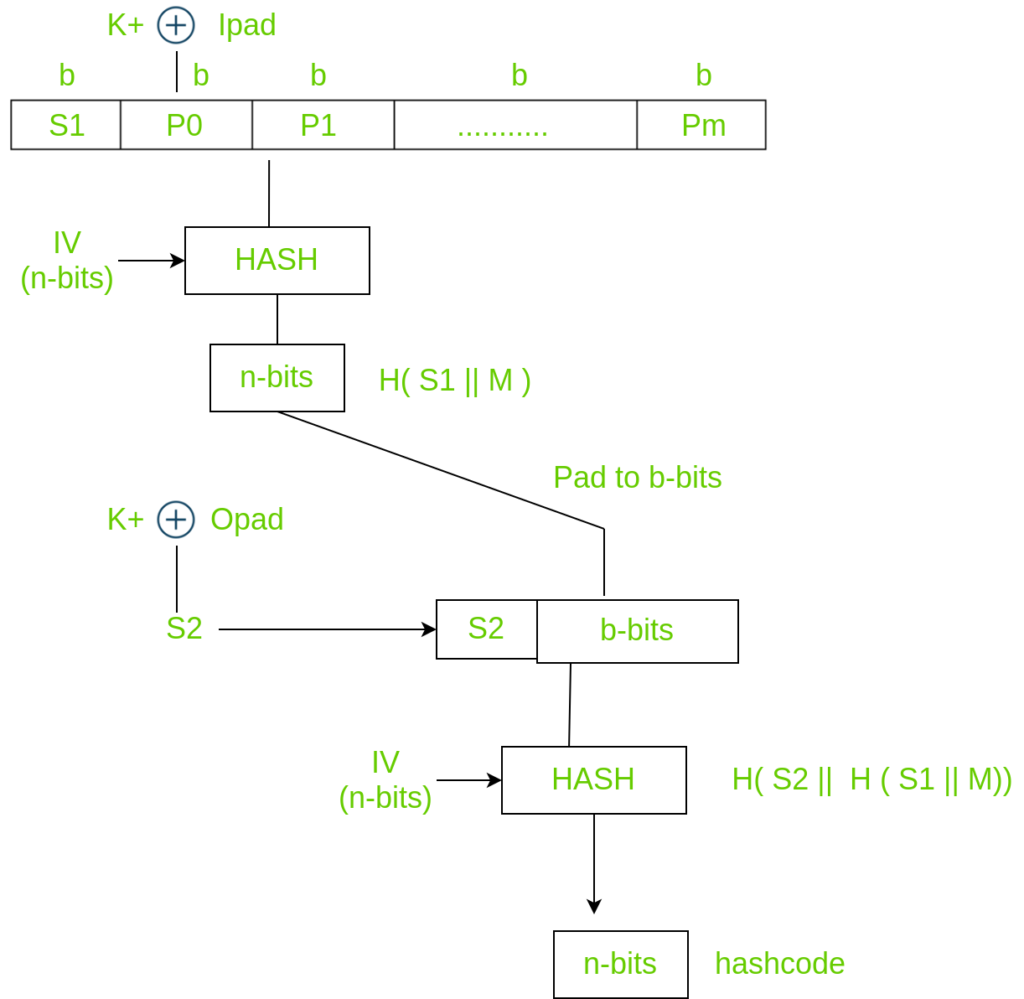
![암호학] HMAC(Hashed MAC) 개념과 과정 암호학] HMAC(Hashed MAC) 개념과 과정](https://blog.kakaocdn.net/dn/1s1Vf/btqEh6BOJV3/Bwk3afhbGhcz4yFKTlWeA0/img.png)